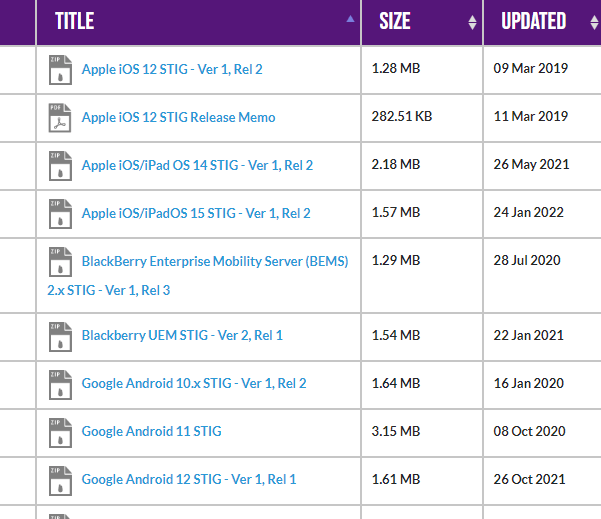
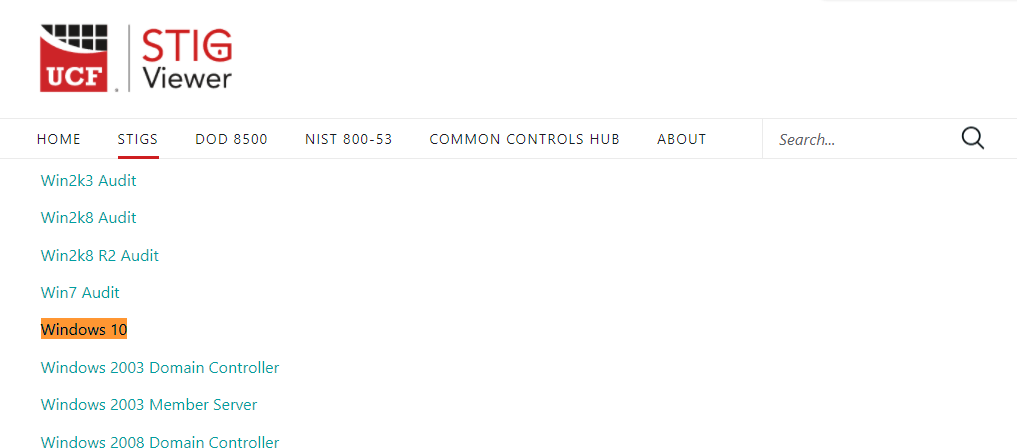
How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems

Top gear Stig Ben Collins reveals show secrets and how Jeremy Clarkson said 'who are you" | Express.co.uk

How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems

EXCLUSIVE: The eight drivers behind Top Gear stunt driver The Stig's famous racing whites | Daily Mail Online

Who is The Stig on Top Gear, when was Ben Collins revealed and has Chris Harris ever worn the white helmet? – The Sun | The Sun

Who is The Stig on Top Gear, when was Ben Collins revealed and has Chris Harris ever worn the white helmet? – The Sun | The Sun
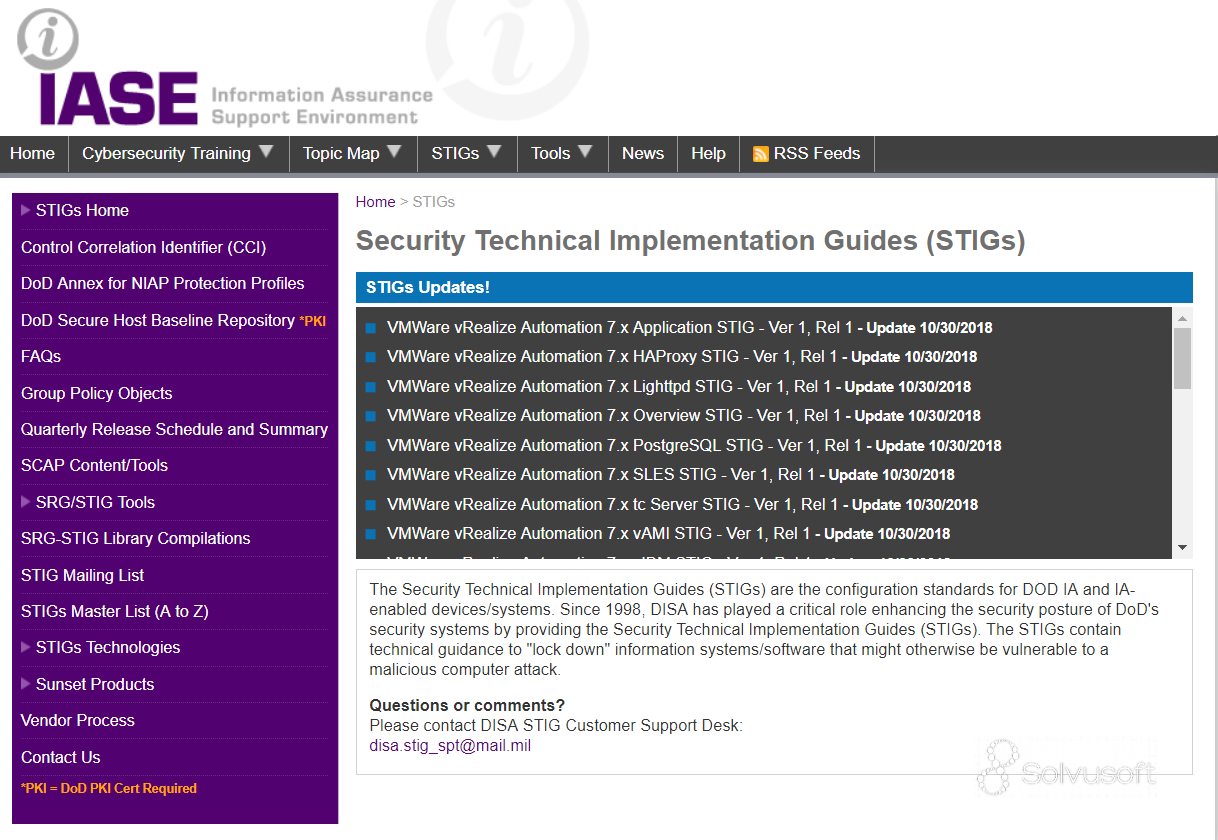
What Is STIG (Security Technical Implementation Guides)? (from DISA (Defense Information Systems Agency))